Current situation: Increased attacks on JGU mail systems!
Cyber attacks are currently increasing both directly on IT infrastructures and on end devices. The majority of attacks are carried out via phishing emails that reach each of us on a daily basis. They are used to infect your computer with malware or to spy out your data.
Currently, emails are circulating in which you are asked to open file attachments or you are taken to websites in order to enter your user data (username/password).
What are phishing emails?
A phishing email is an attempt by fraudsters to steal personal data using a forged email. Another option is to ask users to install malware themselves. The methods are becoming more and more sophisticated, so that some of these emails are difficult to recognize.
How do I protect myself from phishing emails?
How do I know the potential attacks?
- The email contains a link to a fake website that asks for personal information. Currently, it contains a link to a fake university login page.
- Atypical emails (regarding language, style and type of request) are sent from a seemingly known sender with reference to an existing subject or an entire email communication.
- Emails can contain an encrypted zip file as an attachment. The password for decrypting the file is then directly in the email.
- There is a fundamental risk with e-mails that suggest that you transmit personal data such as passwords or payment information.
- Well-known sources (e.g. colleagues, relatives, acquaintances) can also be victims of fraud.
- The sender's display name and the associated email address do not match.
- Emails that contain an urgent request for quick help because the alleged sender is currently abroad or at a conference. When you reply to such emails, you are usually asked to buy prepaid cards e.g. from Amazon in the nearest shop and send the codes to the sender.
- Attacks in the form of wrong appointment invitations.https://www.verbraucherzentrale-bremen.de/pressemeldungen/verbraucherzentrale/gemeiner-datenklau-falsche-outlook-termineinladungen-59533
What can I do against it?
- Keep calm and don't let the sender and subject of the email put you under stress.
- Do not trust dubious offers, vouchers, prizes and products.
- Be careful with e-mails from strange addresses. There can be a dangerous attack behind every link and attachment in an email.
- If in doubt, ask by phone whether the email was actually sent to you.
- Before you click on a link in an email, move the mouse over the link and check which page the link refers to.
- With Outlook the page appears in a small window next to the mouse, with Thunderbird in the footer.
- For all other mail programs and on mobile devices that do not automatically display the target of the link, please do not click this link.
- Do not enter any login data on pages that you have opened by clicking on a link in an e-mail or in an e-mail attachment, unless you are expecting such links and they have been announced in advance (e.g. Seafile links to Data exchange). If in doubt, enter the address manually in the browser.
- No payment service provider will ask customers to enter confidential information via links in e-mails.
- If an e-mail is blocked by the JGU's security systems, do not try to receive this e-mail or the attachment in any other way.
- Please never reply to a suspicious email.
- Delete calendar spam directly. Never cancel or confirm the appointments.
- Further information on the subject of phishing can also be found on the website of the Federal Office for Security and Information Technology (BSI).
- Do I have anything to do with the supposed sender?
If yes: - Am I being addressed personally with correct name, customer number, reference?
- Is the language and spelling correct?
- Do the facts make sense?
If you can answer these questions with No, please delete the e-mail immediately!
What happens if I click on a link to a fake login page?
- You will be asked for your username and password of your JGU account. Do not enter them.
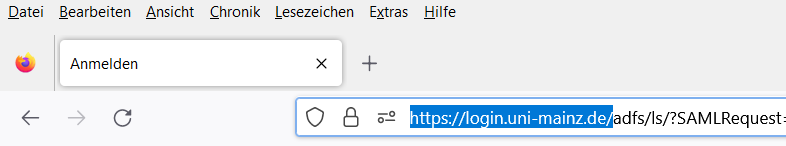
- To make sure it is a legitimate login page, check the URL carefully in your browser.
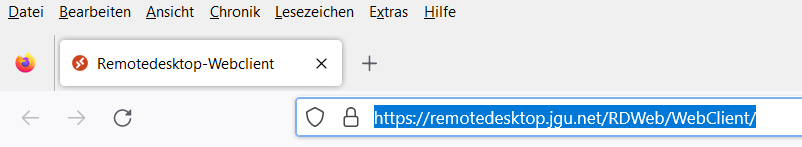
Secure Websites
Login page of the university
Login page for a remote desktop connection
More secure websites
LimeSurvey login page: https://survey.zdv.uni-mainz.de/index.php/admin/authentication/sa/login
Matomo login page: https://webstats.zdv.uni-mainz.de/piwik/
ZDV-Shops login page: https://shop.zdv.uni-mainz.de/
General for more IT security at home
- Use the latest version of the operating system and the programs you have installed. Uninstall unnecessary programs. The fewer applications you use, the smaller the attack surface of your entire system.
- Use virus protection and a firewall BUT do not be misled by activated virus protection or the firewall, they do not guarantee complete security.
- Choose enough “good” passwords..
- Never use the same access data, i.e. the same combination of username and password for different services (Facebook, Uni-Mainz, Amazon).
- Use a password safe (e.g. keepass) to keep your passwords well encrypted in a safe place.
- On the website haveibeenpwned.com you can check whether your e-mail address/password combinations have been stolen from known data theft.
- Change your password if you have recently clicked on a link (which you have not checked beforehand) in an email that took you to a login page.
- Use 2 factor authentication wherever possible.
The Federal Office for Information Security also provides information and recommendations on IT security.
Recommendations for handling hardware and software
- Always install every security update for firmware, operating systems and software on each of your devices immediately.
- Except for administrative purposes, never work with administrator rights, regardless of the operating system. "Normal" users should not be able to install programs.
- Never read e-mails while you are working with administration rights.
- Use local firewalls that only allow outgoing connections, especially when it comes to mobile devices.
- Do not install software from untrustworthy sources.
- Use the latest virus protection software with very frequent virus signature updates.
Trainings
The DATA CON working group of the Institute of Computer Science offers on its site
training courses on the subject of data protection and IT security.